How to Send a Disappearing 'Fleet' on Twitter
After several months in beta, Twitter’s “Fleets” feature is now rolling out to all iOS and Android users. Despite Twitter marketing Fleets as “disappe

Peloton has suffered a data breach. The good news? The information about your exercise habits that subsequently became freely accessible by outsiders isn’t all that damning. Peloton’s delayed response, however, is far more concerning.
As Pen Test Partners described in a recent blog post, a handful of APIs the company uses previously could have been queried by anyone—authenticated and unauthenticated users alike. That was later changed by the company to only permit the former, but that wasn’t much of a protection given that anyone interested in the data could have simply registered for a free Peloton account.
As for what an attacker could scoop up, the available data included:
User IDs
Instructor IDs
Group Membership
Location
Workout stats
Gender and age
If a person was in the studio or not
That’s annoying, but not horrible. There’s not much an attacker can do if they know how much you work out. But it is possible that they could use this information (standalone or in combination with other information provided by other data breaches) to send you a clever phishing attempt.
What is doubly troubling is just how long it took Peloton to respond to reports about these (generally open) APIs. As Pen Test Partners notes:
20
th
January 2021:
disclosed privately to Peloton, as per their [Vulnerability Disclosure Program].
20
th
January 2021:
receipt acknowledged. This is the last we heard from Peloton.
22
nd
January 2021:
we requested an update and offered assistance replicating the vulnerability. No response.
2
nd
February 2021:
unauthenticated API endpoint issue was silently and partly resolved – user data was
now only available to all authenticated Peloton users
. Er…?
2
nd
February 2021:
we asked for an update, given the silent fix. No response.
After 90 days we asked a trusted journalist to speak to Peloton on our behalf.
Said journalist was TechCrunch’s own Zack Whittaker, who ended up publishing a piece on Peloton that finally seemed to get the company’s attention and, more importantly, effect change.
As a security/privacy enthusiast, I find it frustrating to watch things get to that point. While Peloton claims that it was taking action ever since the initial vulnerability submission, it’s just oddly coincidental that the vulnerabilities remained exploitable—scrapeable, really—until one of the biggest publications in tech exposed the problem. Peloton has yet to confirm or deny that the data wasn’t scraped en masse by an outside party, which is ever-more annoying.
Should this entire episode make you throw your Peloton bike in the trash? No. That’s an expensive piece of equipment. However, I’d keep my ear out for news of any future Peloton data breaches; you might have to act on them yourself, rather than wait for Peloton to take the appropriate disclosure steps (and remediation). You might also want to consider obfuscating your data, wherever possible. If it isn’t necessary for your bike ride (or jog), then there’s no reason Peloton needs it—give them a fake birthday, address, name, et cetera. Your competing exercise pals won’t mind.
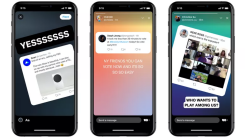
After several months in beta, Twitter’s “Fleets” feature is now rolling out to all iOS and Android users. Despite Twitter marketing Fleets as “disappe

A big thank-you to Apple for exhibiting a bit of restraint with its “best apps of 2020" list; wading through a mere 15 of the best or trendy apps for
Apple is now forcing companies to use its new privacy labels, introduced in December of 2020, if they’re going to keep offering updated versions of th
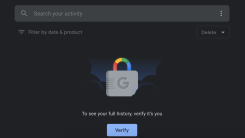
If you don’t want your partner, spouse or roommate snooping on your Google search or YouTube watch histories but you don’t want to resort to using inc

A new security vulnerability has been discovered in the latest versions of Windows that hackers could use to remotely install programs, steal data and

You’re probably not making the most of your Apple Watch if you aren’t using it for fitness, and while you’re exploring this topic, you should consider
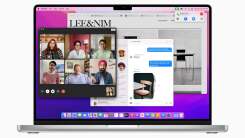
macOS Monterey might seem like nothing but a minor, iterative OS release. On the surface, its biggest new features—SharePlay, Focus, Shortcuts—are all

Instagram started out as a simple photo-sharing app. Now, it seems like it’s anything but. Over the years, it has added so many new features—Stories,
We are a comprehensive and trusted information platform dedicated to delivering high-quality content across a wide range of topics, including society, technology, business, health, culture, and entertainment.
From breaking news to in-depth reports, we adhere to the principles of accuracy and diverse perspectives, helping readers find clarity and reliability in today’s fast-paced information landscape.
Our goal is to be a dependable source of knowledge for every reader—making information not only accessible but truly trustworthy. Looking ahead, we will continue to enhance our content and services, connecting the world and delivering value.